211 Connects Alabama site redesign complete
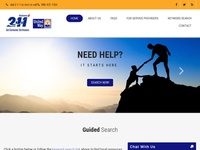
211 Connects Alabama has a new website and it looks great! After only a month of redevelopment, IQ Technologies delivered a modern and fully responsive site redesign which integrates with the state’s 211 software. So far, the feedback from the customer and end users has been outstanding. This is the third project that the United Ways of Alabama has chosen to partner with us, and we hope to continue to be their preferred web designer in the future.
211 Connects Alabama chooses IQ for site redesign
IQ Technologies is honored to have been chosen to redesign Alabama’s state 211 website. 211 is an easy to remember three-digit telephone number assigned by the Federal Communications Commission for the purpose of providing quick and easy access to information about health and human services. In Alabama, the statewide 211 service is managed and operated by the United Ways of Alabama. With this new project, IQ Technologies continues to expand its service offerings into the Alabama non-profit market.
10 Cyber Security Tips for Small Business
Broadband and information technology are powerful factors in small businesses reaching new markets and increasing productivity and efficiency. However, businesses need a cybersecurity strategy to protect their own business, their customers, and their data from growing cybersecurity threats.
1. Train employees in security principles
Establish basic security practices and policies for employees, such as requiring strong passwords, and establish appropriate Internet use guidelines that detail penalties for violating company cybersecurity policies. Establish rules of behavior describing how to handle and protect customer information and other vital data.
2. Protect information, computers and networks from cyber attacks
Keep clean machines: having the latest security software, web browser, and operating system are the best defenses against viruses, malware, and other online threats. Set antivirus software to run a scan after each update. Install other key software updates as soon as they are available.
3. Provide firewall security for your Internet connection
A firewall is a set of related programs that prevent outsiders from accessing data on a private network. Make sure the operating system’s firewall is enabled or install free firewall software available online. If employees work from home, ensure that their home system(s) are protected by a firewall.
4. Create a mobile device action plan
Mobile devices can create significant security and management challenges, especially if they hold confidential information or can access the corporate network. Require users to password protect their devices, encrypt their data, and install security apps to prevent criminals from stealing information while the phone is on public networks. Be sure to set reporting procedures for lost or stolen equipment.
5. Make backup copies of important business data and information
Regularly backup the data on all computers. Critical data includes word processing documents, electronic spreadsheets, databases, financial files, human resources files, and accounts receivable/payable files. Backup data automatically if possible, or at least weekly and store the copies either offsite or in the cloud.
6. Control physical access to your computers and create user accounts for each employee
Prevent access or use of business computers by unauthorized individuals. Laptops can be particularly easy targets for theft or can be lost, so lock them up when unattended. Make sure a separate user account is created for each employee and require strong passwords. Administrative privileges should only be given to trusted IT staff and key personnel.
7. Secure your Wi-Fi networks
If you have a Wi-Fi network for your workplace, make sure it is secure, encrypted, and hidden. To hide your Wi-Fi network, set up your wireless access point or router so it does not broadcast the network name, known as the Service Set Identifier (SSID). Password protect access to the router.
8. Employ best practices on payment cards
Work with banks or processors to ensure the most trusted and validated tools and anti-fraud services are being used. You may also have additional security obligations pursuant to agreements with your bank or processor. Isolate payment systems from other, less secure programs and don’t use the same computer to process payments and surf the Internet.
9. Limit employee access to data and information, limit authority to install software
Do not provide any one employee with access to all data systems. Employees should only be given access to the specific data systems that they need for their jobs, and should not be able to install any software without permission.
10. Passwords and authentication
Require employees to use unique passwords and change passwords every three months. Consider implementing multi-factor authentication that requires additional information beyond a password to gain entry. Check with your vendors that handle sensitive data, especially financial institutions, to see if they offer multi-factor authentication for your account.
Data Storage Strategy Depends on Budget, Data Volume
Ultimately, the combination of storage you need will depend on your volume of data and available budget. Startups with modest data needs and a low budget, for example, could benefit from the Transporter and its minimal equipment costs. Data could be backed up onto a DAS that’s taken offline on a periodic basis.
A business with more substantial storage needs, though, may want to deploy two NAS appliances in separate offices. These could be set to sync with each other over the Internet or VPN. The same arrangement could be made for businesses with only one office, though the second NAS could be a disaster protected one. Data in both cases could be incrementally backed up from one NAS to a cloud storage provider.
Whatever they deploy, businesses generating large volumes of data may find that backing up to the cloud may not be tenable. Such businesses will likely need to invest in a tape drive, with data backed up on tape cartridges kept at an off-site location.
6 Common Data Storage Solutions
Rather than go into every single storage technology that’s available today, it’s better to evaluate the various categories of storage options.
1. Direct attached storage: DAS denotes storage devices that are connected directly to a PC or server, typically using a USB 2.0 or USB 3.0 peripheral port. One weakness of DAS is that you need to do ad-hoc or batch backups to copy data, which means they could contain out-of-date versions of files.
2. Network attached storage: A NAS appliance is a storage device that connects directly to the network. It features the attendant capabilities of a file server and accepts multiple storage drives. Redundancy is offered in the form of RAID capabilities, as NAS supports various file protocols to work directly desktops and laptops. Some NAS models offer the capability to synchronize selected folders or volumes with a second, remote NAS that supports the capability.
3. Disaster protected storage: As its name suggests, disaster protected storage — which can come in the form of DAS or NAS — is hardened against the type of disasters that would have easily destroyed unprotected data. For example, ioSafe says its disaster protected storage appliances can withstand fire for up to 30 minutes and total immersion in water for days.
4. Online storage: While it may seem intuitive to lump all online storage into the same category, there are actually two distinct types of offerings. Some, such as Amazon Simple Storage Service (S3), serve as the cloud version of storage devices for the Amazon Elastic Cloud Compute platform. Then there’s the online storage designed to help consumers and businesses store or back up data in the cloud. For the purposes of this article, that’s what we mean by online storage.
Some of these services, such as MozyPro and SpiderOak, are designed specifically to serve businesses for data backup.
Cloud storage can work very well if backing up data incrementally, and requires no up-front capital investments. The downside, though, is that data retrieval may take an unacceptably long time should you require full data recovery.
5. Private Cloud: Not comfortable with placing their data in the hands of third-party public cloud vendors, some enterprises have taken to building privates version of cloud services to gain some of the inherent benefits of electricity and flexibility. Though this was once out of the reach of small business, innovations mean that small businesses may yet be able to tap into private cloud storage.
The Transporter, for example, is a network appliance that connects to a storage drive to share and synchronize its content. This can be done with client desktops or laptops, and with other Transporter devices. Meanwhile, BitTorrent Sync, currently in beta, lets computers with the correct secret key synchronize directly with one another over the Internet.
6. Offline media: This is commonly understood to be tape drives, but optical media such as DVD and Blu-Ray discs are occasionally used for the purpose of offline data backup. This “technology” may seem outdated, but don’t dismiss it yet: Tape backups have saved Google in at least one Gmail outage, and Facebook is experimenting with Blu-Ray discs for data backup (albeit with a robotic picker handling 10,000 discs in a storage system the size of an entire server rack).
10 IT security risks that small businesses can’t afford to ignore
While small- to midsized businesses (SMB) don’t have the luxury of information security teams and resources that large enterprises can afford, they still face many of the same threats.
Generally thought of as having up to 500 employees, small businesses constitute the vast majority of companies in the United States, making them a critical part of the economy. Their customers naturally expect personal and financial data to be kept secure, and a data breach is a painful and expensive ordeal. Like the larger enterprises, small businesses that accept payment cards have to follow Payment Card Industry rules. It can be daunting for a small business that may not even have an IT department to think about how to tackle network security.
But here are 10 top tips to get started:
1. Business managers need to gain the basic knowledge of where the most important data is held, whether it’s on site in traditional desktops and servers, or in cloud services and mobile devices (including possibly those in “Bring Your Own Device’ arrangements). Whether this knowledge is presented by the in-house IT manager or an outside technology provider, the data storage, access permissions and data processing should be documented, including whatever security controls are in place. There needs to be a conscious decision by business and technology managers, preferably with legal advice, that these security controls are adequate relative to risk. That lays the foundation for what is also needed: a back-up and disaster recovery plan.
2. Bad things happen to good businesses. Floods, fires, earthquakes, the outside thief and the insider threat, and of course malware are all factors that can impact the safety of stored data. Automate the back-up process. Since virtually every business now depends on some form of computer processing, ask the question how employees could proceed if your physical site is suddenly not available. Plan for disruptions that could last weeks if not months — and test it to make sure it’s viable.
3. Train employees about the nature of today’s cyber-attacks. SMBs tend to think that cyber-criminals are going after the really big guys, not them, but that’s simply not true. Cyber-criminals in particular target SMBs to compromise the PCs they use for online banking and payments in order to commit fraud in a big way by emptying out business accounts. Unfortunately, there’s actually less protection for recovery of stolen funds under the law for businesses than for consumers. Banks may even give the small business a hard time, questioning the security it has in place. How does cybercrime often begin? In many cases, the victim opens a “phishing” e-mail message with an attachment laden with malware that will let the attacker begin infiltrating the network. To tamp this down, spam filters should be in place to try and catch phishing e-mails and other junk. But some of it, especially highly targeted, will get through and employees should be trained not to open anything that seems even remotely unusual. Because web-based malware is also commonplace, applying Web-surfing controls on employees’ Internet use is also a good idea. The big companies are starting to use advanced malware protection systems that can track targeted attacks in various ways, and small businesses should too — if it’s affordable. There is also a strong argument to consider setting up a dedicated computing resource strictly for online funds transfer. There are many phone-based social-engineering scams out there now as well and employees need to be wary.
4. Deploy the security basics. That means firewalls for wireless and wired-based access points, and anti-malware on endpoints and servers, acknowledging that traditional signature-based anti-virus is a limited form of defense. Consider technologies such as ‘whitelisting’ to prevent computer software downloads. Over the years, security vendors have frankly conceded they’ve often had a hard time marketing to SMBs, establishing channels of sales and support, and often tried to create editions of their basic products oriented towards fewer numbers of users and less technical expertise to manage them. But some practices are critical for all: Be rigorous about patching all operating systems and applications as quickly as possible. If your business is short-staffed in terms of security expertise, seek outside technical support under a managed security services arrangement. If there’s a malware outbreak, for instance, you will need that expertise. Read articles, join technology user groups, speak with industry colleagues to get tips about outside assistance. Keep in mind that if your business accepts payment cards, it’s mandatory to adhere to the data privacy requirements spelled out in the PCI guidelines, which also includes encrypting sensitive information. The government’s HIPAA and HiTech security rules also require encryption of personally identifiable information in the healthcare industry. Encryption of data at rest and in transit is just a good idea — so why not do it?
5. When disposing of old computers and other devices that store data, remove the hard disks and destroy them. This goes for other types of media, too. And don’t forget paper holding sensitive information as well.
6. Get detailed when it comes to each individual’s access to data. This takes time, but determine what employees or outside business partners really need to have in terms of network and applications to do their jobs. Keep a record of this and consider using more than passwords, perhaps two-factor authentication or even biometrics. This also goes for systems administrators, whose jobs give them huge power over all the information systems in use. Options include requiring a dual-authentication process — something the National Security Agency claims to be doing more vigorously after former NSA tech contractor Edward Snowden leaked all those secrets. Your business is probably not as top secret as the NSA’s, but your internal network and all the most critical data may well be under the control of a sys admin whether you think about that or not. And finally, have procedures for immediate de-provisioning of access and credentials when an employee departs or a business arrangement is altered.
7. Trust but verify, as the old saying goes. Do official background checks on prospective employees to check for criminal history (some companies are even evaluating prospective employees by looking at what their public social media history might indicate about them). And when it comes to technology vendors or cloud service providers, make sure whatever they promise is in a signed contract with some kind of consequences spelled out for failure to deliver. Consider paying a visit to data-center operations operated by business partners with whom you plan to electronically share your customer data, for example, and have them provide details on their security, backup and personnel involved.
8. The era of mobile smartphones and tablets is here and it’s disruptive. Whether a transition to using smartphones or tablets in your business has begun or not, the recognition needs to be there that they represent new operating system platforms with different security requirements and methods of updating and control than older PCs and laptops. Though the mobile-device marketplace is fast-paced in terms of change, both business and IT managers alike should be strategizing on the management and security options — and that includes “Bring Your Own Device” situations where employees are allowed to use their own smartphones and tablets for business. It will mean balancing the security needs of the business with the personal data usage of the individual, who after all, owns the device.
9. Don’t forget physical access in all this. There should be a way to prevent unauthorized individuals from getting near business computer resources. That might mean the cleaning crews at night as well. Challenge unexpected visitors in a polite but determined way.
10. Though the business may be small, think big. Focus on policy. That means devising an employee acceptable-use policy that clearly defines how employees are expected to behave online, how data is to be shared and restricted. Have them read and sign it, making it clear if there’s monitoring of online activities. There should be possible penalties for non-compliance. But just clamping down on employees is not usually a way to encourage the kind of creative thinking and productivity that businesses need in the world where online communications is critical. The challenge is finding the right balance.
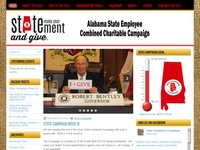
State Website Redesign Complete
We are happy to report that the redesign of the Alabama State Combined Campaign website has been completed ahead of schedule and within budget. This project was a lot of fun and turned out to be a very attractive and functional site. The SCC plans minor website design changes each year to coincide with their unique annual campaign theme, and they intend to partner with IQ Technologies to do it. This site is also hosted on the IQ Technologies server.
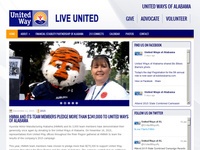
United Way Website Redesign Complete
We are happy to report that the redesign of the United Ways of Alabama website has been completed ahead of schedule and within budget. This project was a lot of fun and turned out to be a very attractive and functional site. This site is also hosted on the IQ Technologies server.
State Combined Campaign to Redesign Website
The State Combined Campaign, headquartered in Montgomery, Alabama, has decided to redesign their web presence, and they have chosen IQ Technologies to spear-head the project. Their decision, along with our recent partnership with the United Ways of Alabama, is further evidence of our commitment to serving the charitable communities of the State. We cannot wait to work with this worthy organization and hope that our service to them is as valuable to their service to the people of Alabama.
United Ways of Alabama selects IQ Technologies
United Ways of Alabama has selected IQ Technologies to redesign their website. It is a major honor for us to be working with an organization such as UWOA that helps so many people through its various charities and programs. I hope that our relationship with UWOA will be a long lasting one and cannot wait to launch the site.






 IQ Technologies
IQ Technologies